User Convenience and Privacy
Securely enable remote employees and contractors on any user-owned PC or Mac with a superior user experience and personal privacy built-in.
The convenience of working on a personal computer is often overshadowed by worries about privacy when company software is involved. We get it – nobody wants their personal activities monitored. Which is why we created Blue Border™. It ensures user privacy while providing maximum flexibility.
Any Device. Anywhere.
User Privacy
What happens in the Blue Border, stays in the Blue Border.
All personal computer activities and data are kept completely separate and secure from anything work-related. Anything end users do personally on their laptop outside of Blue Border cannot be seen, tracked, or monitored by anyone at Venn or their company.
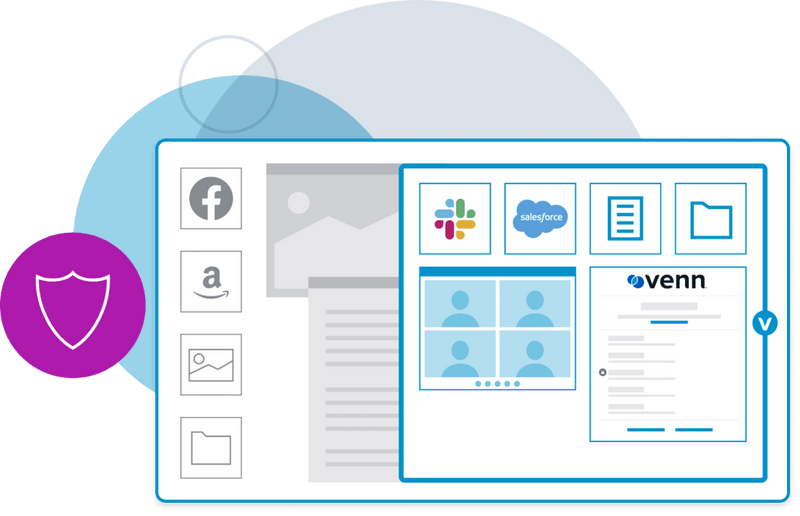
Improved Productivity
Employees can work from anywhere on any device, reducing stress and increasing job satisfaction. Using a device they're already familiar with streamlines tasks and communication, leading to greater productivity.
Work+Life Balance
They can also work outside of Blue Border to take care of personal tasks during breaks or after hours, which supports better time management.
Easy Deployment
Onboard users in minutes. No logging into remote servers to do work or having to carry around multiple laptops.
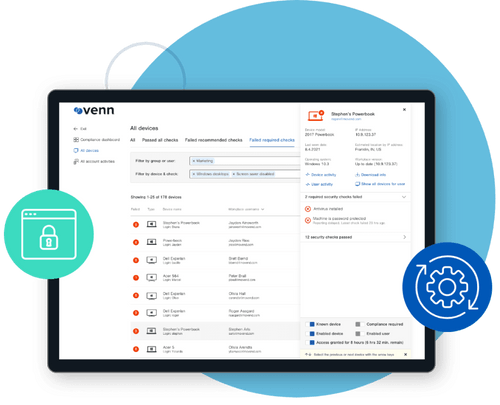
Getting Users Started with Blue Border
To get started, users simply install Venn’s Blue Border onto their computer. Blue Border’s Secure Enclave acts as a container that stores all things work related, including all work applications. When work applications are opened, they will be visually surrounded by a blue border, signaling to users that they are in work mode. This ensures your company’s data remains isolated and protected.
