Why Venn
With Venn, businesses can securely enable BYOD workforces, removing the burden of buying and securing laptops or dealing with virtual desktops.


Companies are Embracing BYOD Workforces
With remote work now a permanent fixture of business, a paradigm shift is underway: the era of the company-issued, locked-down, work-only computer is coming to an end. Many organizations are opting for BYOD workforces, wherein workers are allowed to use their personal computers for work. But legacy security solutions like VDI are expensive and complicated.
A new approach is needed.
Venn Software named as a Sample Vendor for BYOPC in the Gartner® Hype Cycle™ for Endpoint Security, 2023 and in the Gartner® Hype Cycle™ for I&O Digital Workplace Transformations, 2023
The growth of remote and hybrid work has driven a need for a new approach to securing BYO laptops. According to Gartner, "maintaining a robust security posture in environments where user-owned/unmanaged devices access corporate applications and data requires a dedicated BYOPC security initiative."
Gartner, Inc. "Hype Cycle for Endpoint Security, 2023" by Franz Hinner, Satarupa Patnaik, Eric Grenier, Nikul Patel and "Hype Cycle for I&O Digital Workplace Transformation, 2023" by Autumn Stanish, Pankil Sheth
The Venn Advantage



Security and Compliance
Protect company data from exfiltration and stay in compliance with strict industry standards. SOC2, FINRA, SEC, HIPAA, etc.
Alleviate IT Burden
Refocus IT resources on important initiatives, instead of on locking down employee computers or supporting complex VDI.
Cost
Reduce or eliminate the cost of buying, shipping, managing and securing laptops and/or virtual desktop infrastructure.
User Convenience and Privacy
Allow workers to use their personal computer for both work and life with clear separation between the two.
Workforce Agility
Rapidly onboard/offboard remote workers in minutes. Hire any employee or contractor anywhere, on the PC or Mac of their choosing.
Empowering BYOD: Use Case Highlights
BYOD Workforces
Secure Unmanaged and BYOD Devices On Any PC or Mac
Virtual Desktop Alternative
Eliminate Infrastructure Complexity and Reduce Costs

Work & Personal on One Device
Employee Productivity Improves Business Results
MDM for Laptops
Control, Secure And Administer Policies On Any BYOD Laptop
Contractors & Offshore Workers
Secure Sensitive Client Assets & Meet Compliance
Revolutionizing How Businesses Enable BYOD Workforces
Purpose-built features to secure remote workers on unmanaged devices.
|
VDI, Cloud PCs, DaaS |
Browser-only | Company Managed |
|
|---|---|---|---|---|
| Security and Compliance
Provide a single point of access for all work apps, files, and websites. |
||||
| User Convenience and Privacy
Allow users to use a single computer for both work and life without impacting their user experience or performance in any way. |
||||
| Cost
Cut down on HW and management costs for remote employee computing devices. |

|
|||
| Control
Enable centralized security, IT policies and remote management of devices. |

|

|

|
|
| Easy Deployment
Self-service deployment and easy integration with 3rd party IT and security software. |

|
|||
| Remote Work at Scale |
See why customers
love Venn
Industry Recognition







Over 700 Organizations Trust Venn

Windows/Mac.

Puts virtual wrapper
around it.
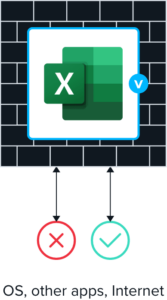
Controls what goes in and
out.
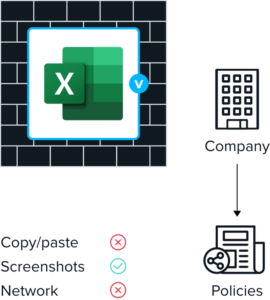
entitlements.






