When remote employees and contractors use personal laptops for work, being asked to install security software can raise concerns about employer surveillance of personal activities. This unease stems from a natural desire for privacy—nobody wants their company to have access to their personal digital life.
In this blog post, we’ll discuss how IT teams and companies can tackle this challenge while still meeting the need for security, compliance, and productivity monitoring. We’ll explore how to implement effective monitoring on BYOD laptops, ensuring security without compromising employee privacy. This includes a closer look at the people, processes, and tools required to strike the right balance.
Employees’ Concern for Their Privacy
Recent years have seen a surge in privacy awareness, largely driven by landmark legislation like the GDPR in Europe and the California Consumer Privacy Act (CCPA) in the United States. These laws have shed light on the extent of data collection and usage by organizations, prompting individuals to question their digital footprint both in their personal lives and at work.
For example, they’ve all experienced targeted marketing campaigns, which customize ads based on words they’ve searched for online, groups they’re in and their demographics. Many of them are acutely aware of how their online activities are tracked, analyzed and monetized. It’s natural for this awareness to spill over into our professional lives, leading employees to wonder about the level of scrutiny applied to their BYOD devices.
Online conversations are a good place to get a sense of that concern. Platforms like Reddit host numerous threads where employees share their concerns about company surveillance on their personal devices.
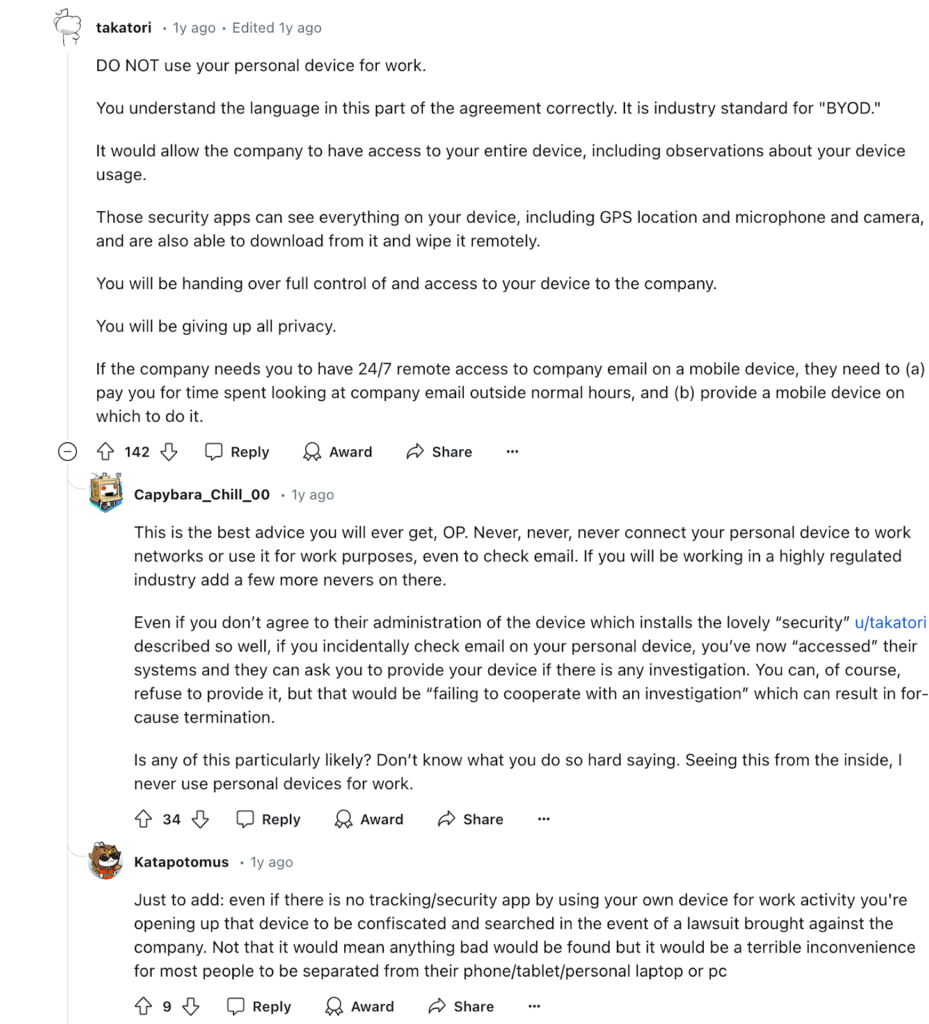
And it’s not just employees who are suspicious. Real-world incidents have brought this issue into sharp focus. Wells Fargo has reportedly fired workers for simulating keyboard activity to appear active while working remotely. This incident underscores that companies not only have the capability to monitor employee activity but are also willing to take action based on that information, further creating panic and stress among employees. And if some employees can “live” with the idea of monitoring on professional devices, monitoring on BYOD is a frog that is much harder for them to swallow.
The Two Faces of Monitoring
When it comes to employee monitoring, companies generally fall into one of two categories:
- Monitoring for Productivity, Security, and Compliance
Companies in this category implement monitoring systems primarily to:
- Ensure productivity and efficient use of company resources
- Protect sensitive information and intellectual property
- Prevent cybersecurity threats
- Comply with industry regulations and legal requirements
These organizations typically have clear policies about their monitoring practices and use the data collected to improve overall business operations rather than to micromanage employees.
- Monitoring for Tracking Employees
On the other hand, some companies take a more invasive approach, using monitoring tools to:
- Track individual employee activities in detail
- Measure time spent on specific tasks or websites
- Monitor communication content, including emails and messages
- Evaluate performance based on digital activity metrics
This approach can create a culture of mistrust and may infringe on your contractors’ and employees’ privacy rights.
What Kind of Company Do You Want to Be?
If your company falls into the first category – monitoring for productivity, security and compliance – which most companies do, it’s important to be transparent with your contractors and employees. Transparency builds trust, alleviates concerns and fosters a positive work environment.
Here’s how you can achieve this through the three Ps: People, Processes and Products.
People: Building Accountability and Trust
The foundation of a healthy workplace is trust in your team: employees and contractors. It’s important to build a sense of accountability and pride among your team, encouraging them to take ownership of their responsibilities. When it comes to monitoring, show them that monitoring is not intended for spying on them. In addition, show them you trust them by sharing how monitoring takes place and why.
Human Resources can play a pivotal role in this process by:
- Thoroughly addressing concerns about monitoring
- Facilitating open discussions about workplace monitoring and its purposes
- Providing training on company values and business expectations
- Ensuring that contractors feel like an inherent and trusted part of the team
Processes: Communicating Trust and Respect
Your monitoring policies should emphasize trust and respect while enhancing workflows and contributing to organizational goals. Here’s how to communicate these processes to employees:
- Explaining how monitoring helps protect the company and their devices from cyber threats
- Demonstrating how data gathered helps improve overall productivity and workflow efficiency
- Showing how compliance monitoring protects the company from legal issues
- Providing periodic reports on how monitoring data is being used to improve the workplace
Products: Choosing Tools that Protect Employee Privacy
The final ‘P’ in our framework is Products – the actual tools and technologies you use in your stack. We recommend resisting the temptation to implement every tracking tool available. Instead, carefully evaluate your needs and choose only those tools that are truly necessary for your business operations, security and compliance requirements, and can really enable BYOD workforces. This targeted approach helps prevent overwhelming your team with excessive monitoring and demonstrates your commitment to respecting their privacy.
For productivity, it’s recommended to select products that provide valuable insights to improve performance, streamline tasks and reduce workload. The goal should be to use data to enhance the work experience, not to micromanage. Look for tools that empower employees and contractors to manage their own productivity, fostering a culture of self-improvement and autonomy.
For security, consider implementing technologies like Blue Border, which demarcates work activities from personal ones. This approach ensures that personal activities are not tracked, respecting employee and contractor privacy on their own device while maintaining necessary oversight of work-related tasks. It’s a concrete way to demonstrate your commitment to balancing monitoring needs with employee privacy.
By choosing products with these characteristics, you send a clear message that the purpose of monitoring is to support and empower your team, not to police them or take advantage of their own devices.
Conclusion
Your team is your most valuable asset, and addressing their concerns will help you build trust and loyalty that will be repaid and make your business thrive. Privacy-related worries are prevalent, and it’s better to be transparent and foster communication rather than to let frustrations pile up. By encouraging open communication, creating clear policies, demonstrating the use of data and implementing tools responsibly, you can continue to monitor while instilling confidence among your employees and contractors.
Solutions like Venn’s Blue Border protect work-related activities and the endpoint while creating isolation between work and personal on BYOD. This means workplaces cannot gain access to private employees’ actions, even if they wanted to. This ensures security while alleviating employee worries about their privacy.



